Save millions on device costs
$11.5M
Without platform
$766K
When using Dispel
$10.7M
Saved in device costs
For Industrial Monitoring and Heavy Equipment sectors, the average salary for a professional operations administrator in the U.S. is $46/hour.* Using the right IoT service platform can cut device management time significantly, reducing the need for interaction from five times to just twice annually, thereby saving on labor costs.
* Based on Q2 2024 data for 113,671 records from 821 companies valued between $100M - $250M averaged across all US locations (national average).
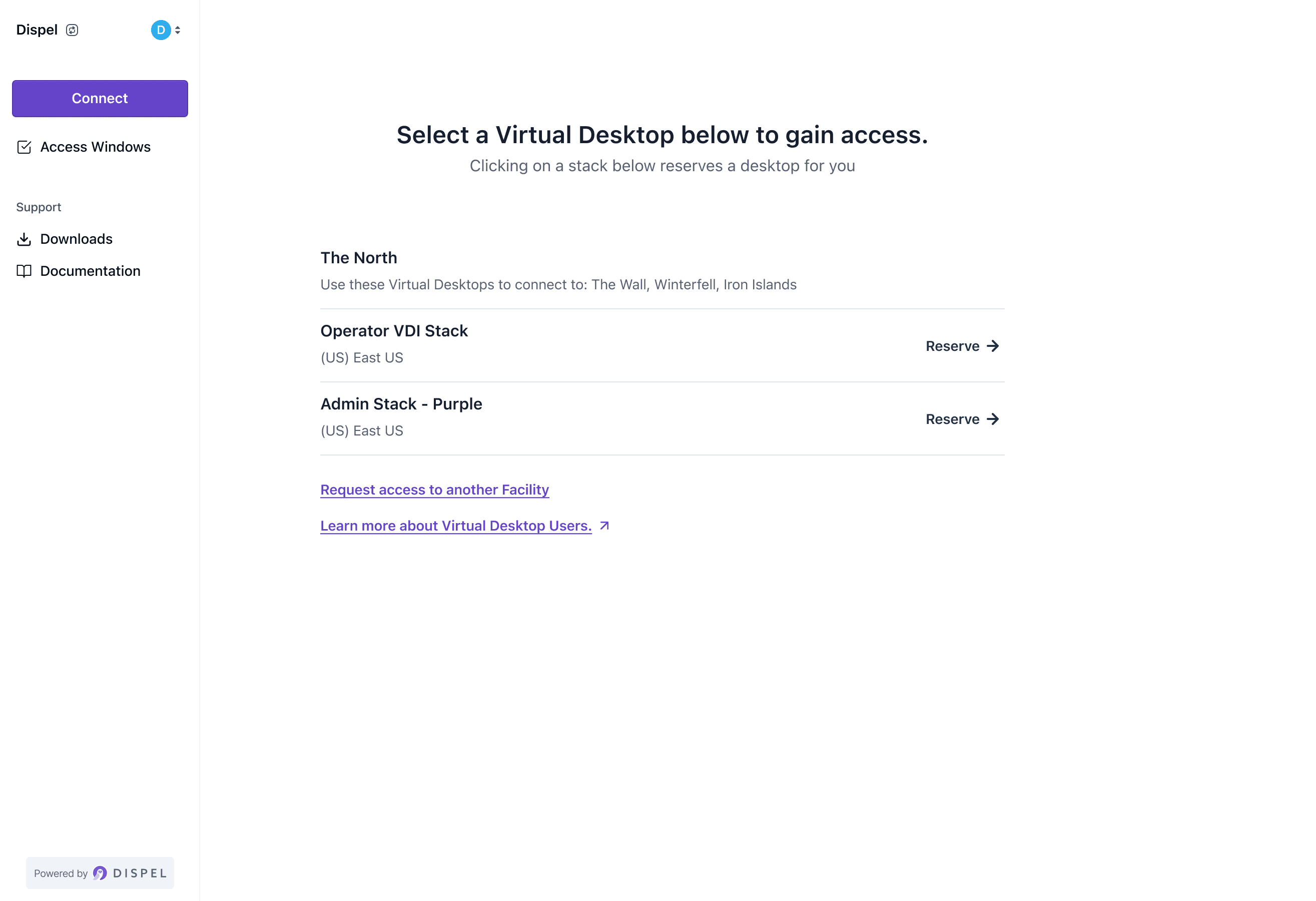
How do we do it?
Our approach is to secure every endpoint. With multiple layers of authentication, we add the necessary defenses for your network.
More Capabilities for Improved Security
Dispel has a broad range of features designed to complement and elevate your core experience, enabling secure workflows and increased visibility.
Case Studies

Seadrill is a leading offshore drilling company, with a fleet of ultradeep water drill ships available for deployment worldwide.
Using Dispel's Zero Trust Access features, Seadrill no longer has to fly personnel out to their vessels. Instead, teams can respond and monitor remotely in minutes.
Seadrill uses Dispel's certifications to win business by demonstrating superior cybersecurity compliance.
Dispel secures and enhances any industry
Our Zero Trust Access platform enables businesses across multiple industries to securely and remotely monitor network access for their manufacturing facilities.

Car and truck manufacturers centralize control and simplify access workflows using Dispel’s platform.

Chemical engineering companies use Dispel to maintain manufacturing access, security, and visibility.

Manufacturing operations achieve centralized control with Dispel products.

Cosmetic corporations are using Dispel to control, monitor, and verify access for every connection.

Dispel enables energy providers to increase their response times by enabling remote facility maintenance.

Food and Beverage companies centralize control and increase visibility into external access.

Healthcare technology companies provide training environments and networking with our products.

We allow Oil & Gas companies to remotely monitor and access their vessels, allowing rapid response times.

Water and Wastewater facilities have improved security and visibility of their system access when using Dispel.
Our Zero Trust solution covers all machine types in industrial environments. With no touch support for all TCP/IP protocols including SSH, VNC, RDP, and Telnet.

Industrial PC
Remote access enables technicians to manage these durable computers from afar, minimizing maintenance trips. Data streaming allows for immediate analysis and action based on live operational data.

DCS
DCS benefits from remote adjustments, optimizing processes without on-site presence. Streaming data aids in real-time process efficiency and energy management.

HMI/PLCs
Remote HMI/PLC access facilitates quick adjustments and monitoring, while data streaming offers insights for remote troubleshooting and efficiency enhancements.

SCADA
Remote SCADA access streamlines the oversight of dispersed systems, with data streaming providing instant operational insights for better decision-making.